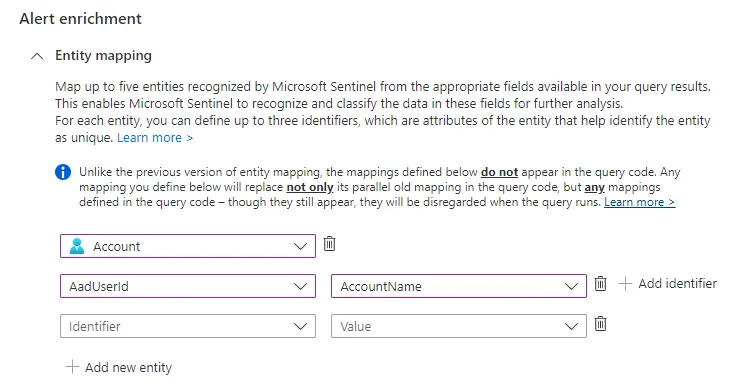
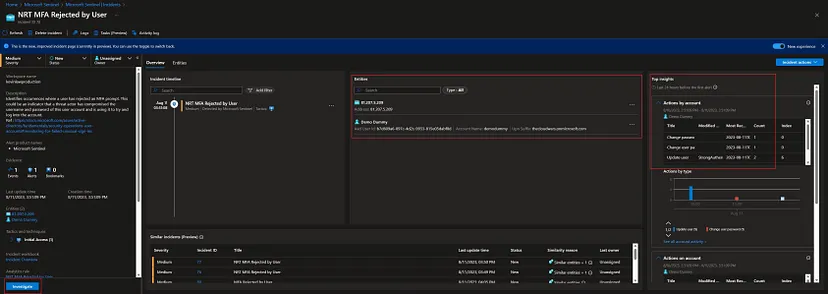
As more SIEM/SOAR activities center around identity and entities within a company’s infrastructure, enriching alerts and incidents within the SIEM with the right entity mapping has become critical for SOC analysts to do their work properly. Benefits of having the right entity mapping within Microsoft Sentinel Analytics Rules include a reduction in alert fatigue among SOC staff and more possibilities for automation which centers around entities which are involved in the alerts/incidents (my following blog post series will concern this topic).
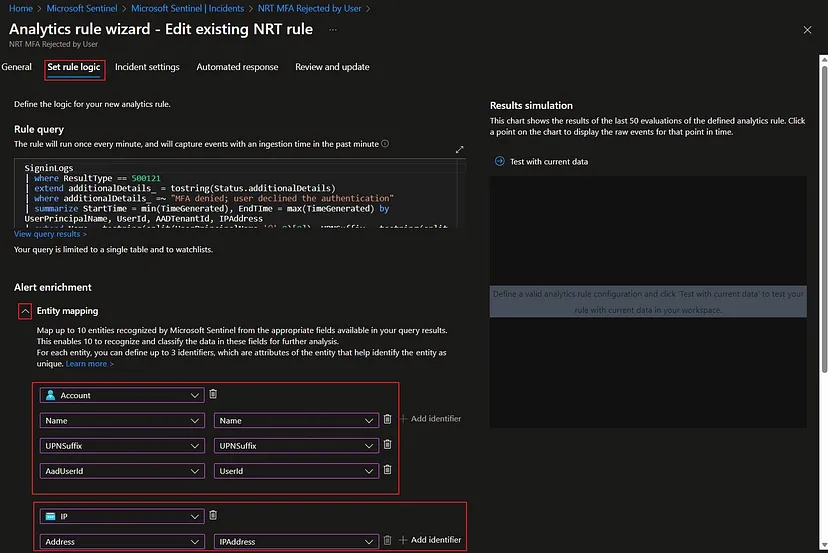
The introduction of the Microsoft Sentinel Content Hub has made it significantly simpler to deploy quality content such as analytics rules, playbooks and hunting queries. However, some of the analytics rules deployed from the content hub might not provide the exact entity mapping which is desired for your Sentinel deployment and SOC operations. Additionally, you might want to extend the entity mapping of your selfmade analytics rules. I will provide three different entity mapping scenarios in increasing order of complexity. Let’s start off this blog series with a simple example for the entity mapping of a user account which is involved in an incident.
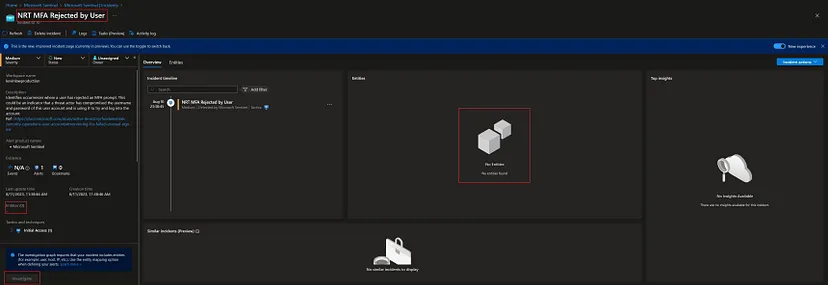
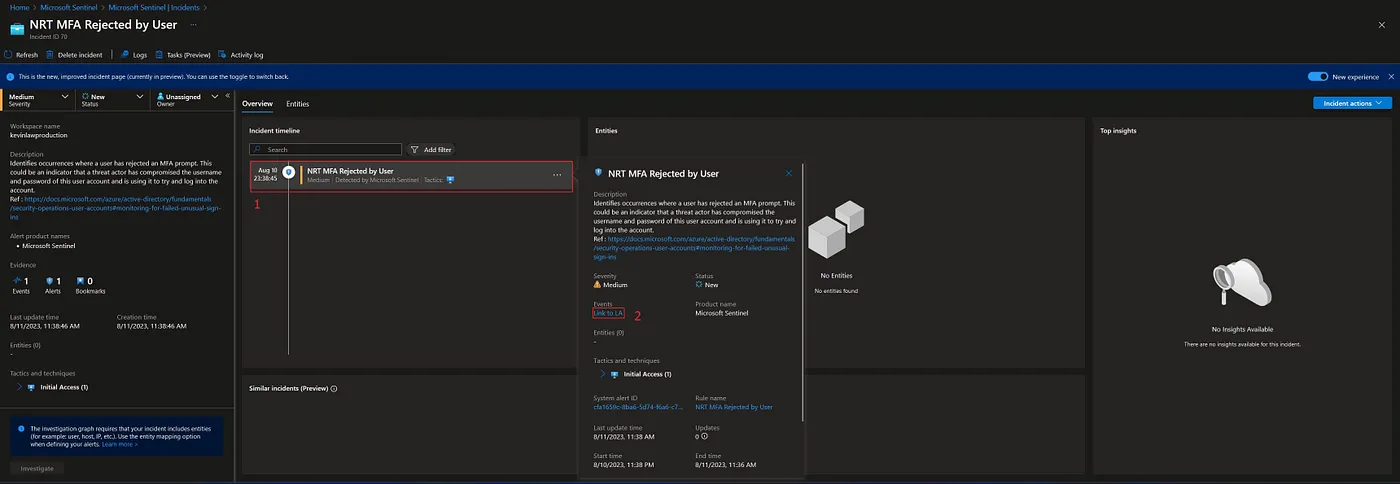
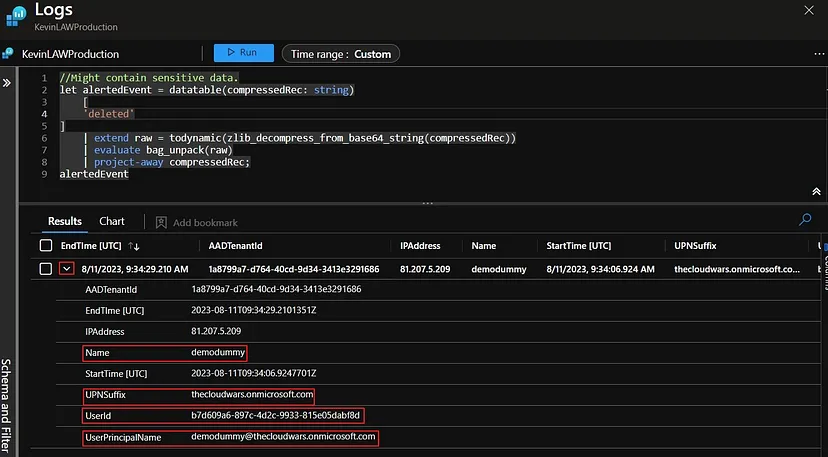
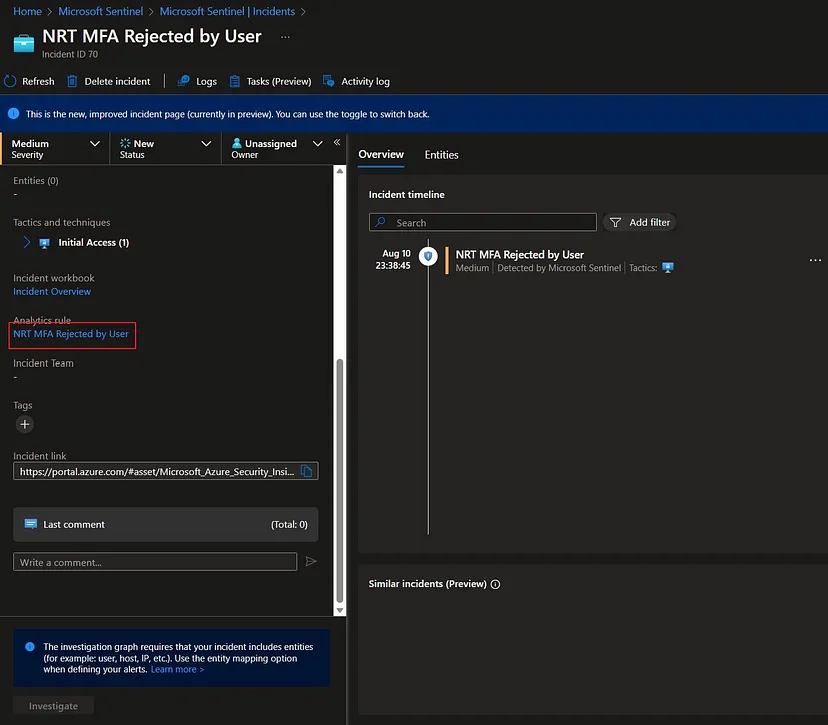
We have received the following NRT MFA Rejected by User incident in our Sentinel instance: